We work to advance the practice of teaching cybersecurity through curriculum development and strengthening the profession and practice of teaching cybersecurity.
Curriculum Guidelines - HSCCG
- prepare students to study cybersecurity in college, and
- develop a high school cybersecurity program that can qualify for early college credit.
The development of the Cybersecurity Curriculum Guidelines was funded by The National Cryptologic Foundation (NCF).
Download the High School Cybersecurity Curriculum Guidelines here.
DARK Enterprises By The Numbers


The Teach Cyber Curriculum
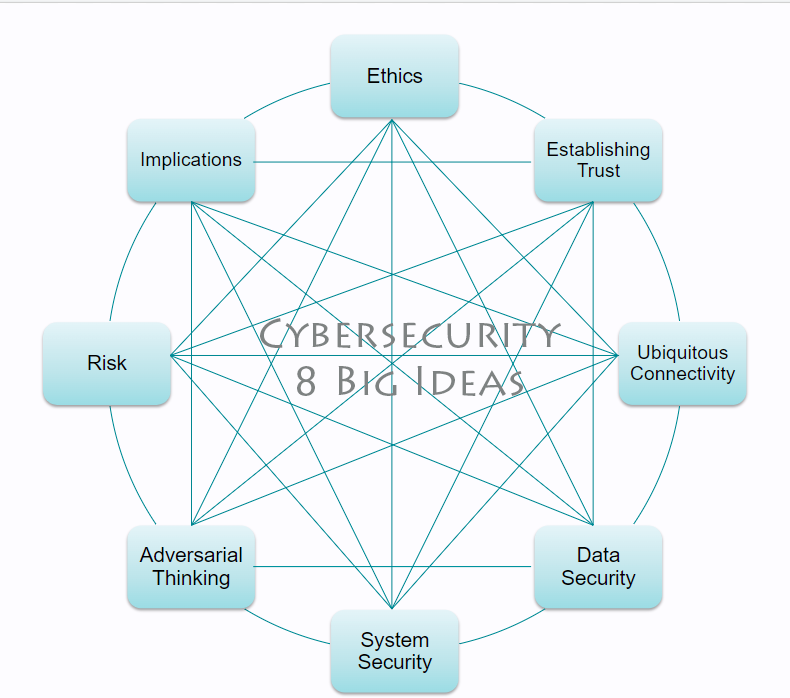
This is a year-long, introductory cybersecurity course. The overarching goal of the course is to introduce students to the foundational concepts, principles, and tools of cybersecurity. The course is centered on the Cybersecurity Curriculum Guidelines and is thus situated in eight big ideas: ethics, establishing trust, ubiquitous connectivity, data security, system security, adversarial thinking, risk, and implications.


After this course, students will:
- understand that cybersecurity has broad implications and ethical reflection and judgment are required.
- understand the fundamental cybersecurity principles necessary to determine security requirements and mechanisms.
- study historical events and their cybersecurity implications; relevant laws and policies governing data; and economic concerns and risk management trade-offs involved in making cybersecurity decisions from various stakeholder perspectives.
- learn to challenge assumptions and practice thinking about opposing forces to analyze threats, vulnerabilities, and attacks.
- evaluate the tools used to connect cyber-physical systems
- practice using the encryption techniques needed to secure data across networks.
The Teach Cyber Curriculum has 8 modules. You can use all or some of the curriculum. Our curriculum was built to be modular.
| Units | Estimated Number of Days |
|---|---|
| What is Cybersecurity | 11 |
| Risk, Adversity and Trust | 17 |
| The Elements of Cyberspace | 20 |
| Data, Software, Hardware, and Network Security | 25 |
| Countermeasures Against Cyberattacks | 33 |
| Security is Not Free | 8 |
| Threats, Vulnerabilities, and Attacks: A Closer Look | 15 |
| States, Stateless, Sovereignty and Cybersecurity | 15 |
| Labs | N/A |
The Teach Cyber curriculum is modular so the units and lessons can be arranged and rearranged to fit the needs of your school and your students. Here are a few suggestions from the creators and users of Teach Cyber about how to sequence the units and lessons to make a course.
Semester Long Course with no Prerequisite Knowledge Using the US Cyber Range – 15 Weeks, ~65 contact hours
| Course Outline | Teach Cyber Unit | Estimated Time |
|---|---|---|
| Part 1: Introduction to Cybersecurity | What is Cybersecurity Unit | ~9 contact hours |
| Part 2: Technical Basics | The Elements of Cyberspace Unit | ~15 contact hours |
| Part 3: Doing Cybersecurity | Data, Software, Hardware, and Network Security Unit and Countermeasures Against Cyberattacks (note, these are long units, so you will have to select lessons from each) | ~39 contact hours |
| Part 4: Tying it Together | Risk, Adversity and Trust – Lesson 6 | ~ 2 contact hours |
| Course Outline | Teach Cyber Unit | Estimated Time |
|---|---|---|
| Part 1: Introduction to Cybersecurity | What is Cybersecurity Unit | ~9 contact hours |
| Part 2: Doing Cybersecurity | Data, Software, Hardware, and Network Security Unit and Countermeasures Against Cyberattacks (note, these are long units, so you will have to select lessons from each) | ~46 contact hours |
| Part 4: Tying it Together | Security is Not Free States, Statelessness, Sovereignty and Cybersecurity – Lesson 2 Risk, Adversity and Trust – Lesson 6 | ~ 10 contact hours |
Year Course without Cyber Range Access (50 min/day and 135 hours of instruction)
Supplement the course with activities (~50 hrs) from picoGym and picoCTF. PicoCTF includes challenges from six domains of cybersecurity including general skills, cryptography, web exploitation, forensics, reversing, binary exploitation (https://primer.picoctf.org/ ). CyberStart America is another source of activities.
| Course Outline | Teach Cyber Unit | Estimated Time |
|---|---|---|
| Part 1: Introduction | What is Cybersecurity Unit Risk, Adversity and Trust Unit (omit Credential Harvesting Lab) | ~10 contact hours ~18 contact hours ~15 contact hours Supplemental activities |
| Part 2: Practicing Cybersecurity | Data, Software, Hardware & Network Security Unit (omitting 6 Cyber Range labs)
Countermeasures Unit (omitting 10 Cyber Range labs) CTF participation | ~18 contact hours ~25 contact hours ~35 contact hours Supplemental activities |
| Part 3: Tying it Together | States, Statelessness, Sovereignty and Cybersecurity Unit | ~15 contact hours |
[1] Teachers often ask us how which lessons to select in order to use Teach Cyber in a semester long course. Here is our #1 suggestion: when making selections, be sure to includes lessons from BOTH units because they work together. The Unit on Data, Software, Hardware and Network Security focuses how threats sources exploit vulnerabilities to create attacks. The Unit on Countermeasures Against Attacks focuses on preventing and detecting attacks. So if you are teacher looking to choose lessons, be sure to include lessons that teach students how to think about the cycle of threat sources use vulnerabilities to launch attacks, and cybersecurity professionals use countermeasures to try and prevent that from happening and to detect it when it is happening.
Cyber Discovery Kit
The Cyber Discovery Kit (CDK) is available for download as a pdf. In the CDK the 8
Big Ideas of Cybersecurity (Ethics, Trust, Ubiquitous Connectivity, Data Security,
System Security, Adversarial Thinking, Risk, and Implications) are introduced.
Students explore key principles and concepts and investigate cybersecurity
vocabulary and careers. The purpose is to help students discover the vast field of
cybersecurity.
The CDK is designed for 6th to 9th grade students in a club or classroom setting to heighten interest in your cybersecurity course, program, or pathway. Additionally, we hope that the experience allows students to reflect and make healthy, safe, and ethical decisions in cyberspace.
Contact sabrina.smiley@darkenterprisesinc.com if you have questions.

NCTA
NCTA is a 12-credit hour graduate certificate for high school teachers. It includes coursework on teaching cybersecurity, foundations of cybersecurity, network security, and advanced topics. Four universities (DePaul University, University of Louisville, University of Arkansas-Little Rock, and California State University-Sacramento) will be offering the virtual program, with variation depending on the university’s program.
NCTA is supported by a grant from the NCAE-C , which is the National Centers of Academic Excellence in Cybersecurity (located within the National Security Agency).
Wyoming Teach Cyber Project
The WY Teach Cyber project will result in two online, asynchronous teacher professional development courses ( introductory and advanced 15-hour courses) to support Wyoming teachers in their journey toward teaching cybersecurity. Teachers will have the opportunity to take an end-of-course assessment and earn a WY Teach Cyber badge/certificate to indicate successful completion of each course.
The courses will meet the Quality Standards for Continuing and Professional Education and will be QM-certified, as well as being aligned to the Wyoming Computer Science Content and Performance Standards.

Cisco NetAcademy
Our partnership with Cisco NetAcademy provides free cybersecurity training for educators. Teachers self-enroll in courses and the training is self-paced. Badges are awarded upon completion.
If you are interested in the need for cybersecurity, privacy, and common attacks and protections start with the Cybersecurity Basics course. If you want to develop a broad foundational understanding, we recommend the Cybersecurity Essentials course. When you are ready to develop your understanding of networks, dive into the Networking Essentials course. The Packet Tracer course will introduce this network design, simulation, and modeling tool.



